
DOM.PL™ Projekt domu DN ARMANDA XS BIS CE DOM PC167 gotowy koszt
What is DOM-based cross-site scripting? DOM-based XSS vulnerabilities usually arise when JavaScript takes data from an attacker-controllable source, such as the URL, and passes it to a sink that supports dynamic code execution, such as eval () or innerHTML.
ARMANDA XS BIS 119,52 M2 Moduł Koncept Opole Domy Modułowe
DOM-based XSS: This more advanced vulnerability exists in client code and not on the server code. DOM-based XSS is neither reflected nor stored onto the server, but exists in a page's Document Object Model (DOM).

Pin on Stefi
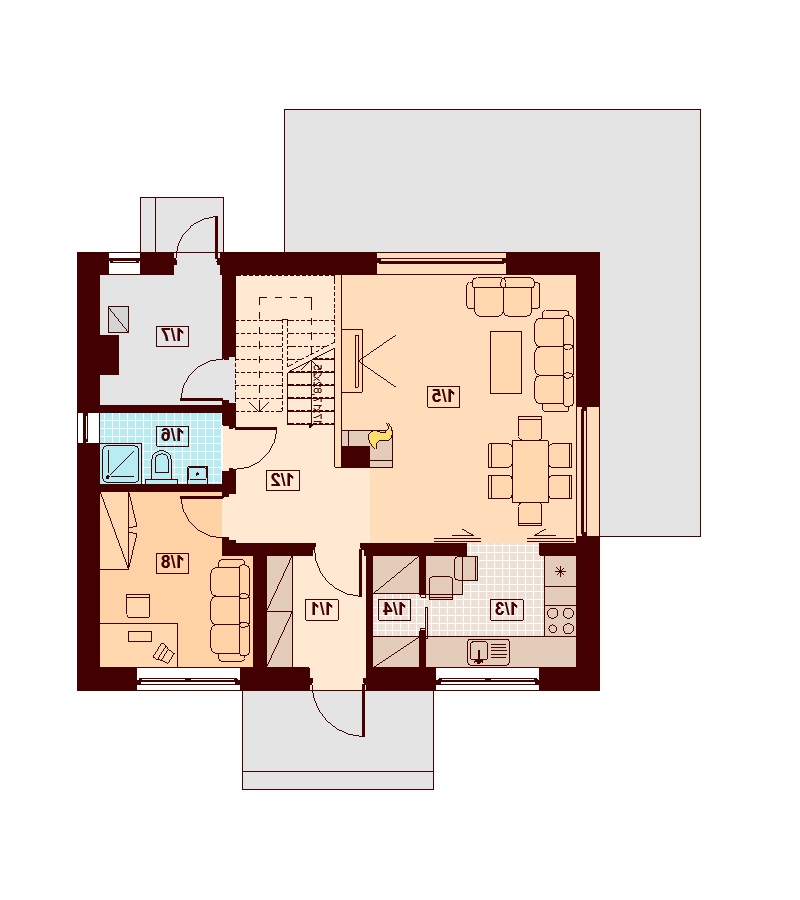
Przedstawiamy Państwu dom jednorodzinny wolnostojący wg projektu Armanda Mała BIS w miejscowości Wola Rzędzińska.Powierzchnia użytkowa domu to 114,76 m2. Dom.

Projekt domu Armanda XS 102,9 m2 koszt budowy EXTRADOM
DOM-based XSS, also known as Type-0 XSS, is an XSS attack in which the attack payload is executed by altering the DOM in the victim's browser. This causes the client to run code, without the user's knowledge or consent. The page itself (i.e. the HTTP response) will not change, but a malicious change in the DOM environment will cause the.

Pin on Stefi
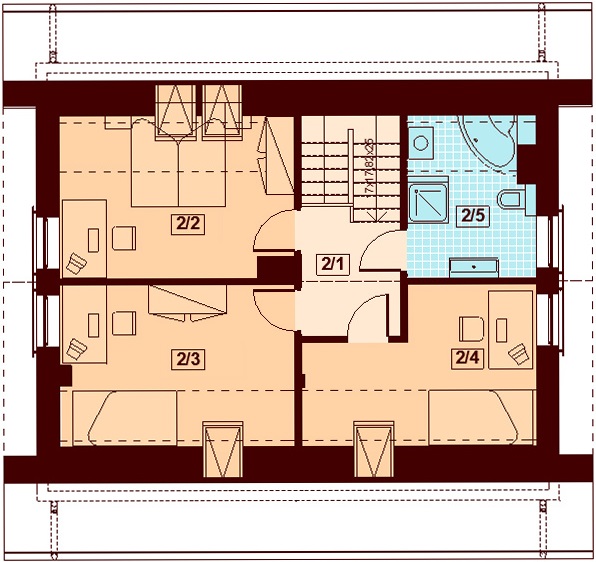
Projekt Armanda XS Bis ma 100 m2 i poddasze użytkowe. 隣 Dzięki prostej bryle i dwuspadowemu dachowi. ️ Idealny domek dla 4⃣-osobowej rodziny. Projekt Armanda XS Bis ma 100 m2 i poddasze użytkowe. 隣 Dzięki prostej bryle i dwuspadowemu dachowi.

Пин на доске Projekty domów
In particular, DOM-based XSS is gaining increasing relevance: DOM-based XSS is a form of XSS where the vulnerability resides completely in the client-side code (e.g., in JavaScript). Indeed, more and more web applications implement all of their UI code using fronted web technologies: Single Page Applications (SPAs) are more prone to this.

Armanda XS
Projekt domu Armanda XS WOK1026 REKLAMA 1 /5 Pokaż odbicie lustrzane Warianty i podobne Szacunkowy koszt SSZ 229 000 zł Projekt z Budową Wybierz wygodę - gotowy dom nawet w 6 mies. z gwarancją ceny Cena projektu: 5 590 zł Kup projekt Projekt jest dostępny Masz pytania? Zadzwoń 71 715 20 60 pon.-pt. 8-21, sob. 9-17

Pin on Salon
Czy ktoś na grupie buduje dom Armanda XS. Ciekawa jestem jak wykonaliście sufity w pokojach na piętrze z balkonami. Ciekawią mnie skosy. Pochwalcie sie zdjęciami

Projekt domu Armanda XS Bis (TZW133) 100.64m²
Zobacz projekt domu na stronie: https://www.extradom.pl/projekt-domu-armanda-xs-bis-WOK1068

DOM Armanda
Armanda xs odbicie lustrzane

Blog MojaBudowa.pl dziennik budowy, katalog firm budowlanych
👍👍👍 and subscribe for more DOM XSS tutorials: https://www.youtube.com/channel/UC2vVVgKKzN-Gb_xeaUY0o-Q?sub_confirmation=1Check out my best selling AppSec.

DOM.PL™ Projekt domu DN ARMANDA XS BIS CE DOM PC167 gotowy koszt
Projekt Armanda XS oferujemy z kosztorysem inwestorskim GRATIS. Jest to domek z poddaszem użytkowym odpowiedni dla 4⃣-osobowej rodziny. Ma 102 m2 powierzchni użytkowej. Na parterze.
Armanda XS BIS
DOM Invader is a completely new Burp Suite tool, implemented as an extension in the embedded browser. Simply update your version of Burp Suite Professional or Burp Suite Community Edition to 2021.7 on the Early Adopter channel to start using it. View the latest release notes. By default, DOM Invader is turned off (because it alters site behavior).

Armanda XS (WOK1026) 3D model by extradom.pl (extradom) [2d5cf84
Visit Sandra Armando's profile on Zillow to find ratings and reviews. Find great San Jose, CA real estate professionals on Zillow like Sandra Armando of Sorrento Properties, Inc.

Pin on Plan casa
A DOM-based XSS attack is also conducted by tricking a victim into clicking a malicious URL. Sources and sinks in DOM-based cross-site scripting. Every DOM-based XSS vulnerability has two elements: the source of user input and the target where this user input is written, called a sink.

Projekt domu Armanda XS BIS House exterior blue, Facade house, Small
A DOM-based XSS attack is possible if the web application writes data to the Document Object Model without proper sanitization. The attacker can manipulate this data to include XSS content on the web page, for example, malicious JavaScript code.